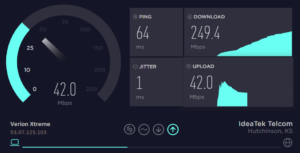
Speed Test App
IP Reputation & Threat Intelligence
Reputation of IP Addresses
IP reputation refers to the assessment of the trustworthiness and past behavior of an IP address on the internet. It is a concept used in cybersecurity to evaluate whether an IP address has been involved in malicious activities, such as spamming, distributing malware, participating in cyber attacks, or other forms of cyber threats.
IP reputation is crucial in filtering and blocking potentially harmful traffic. Security systems often maintain databases or lists of IP addresses with known reputations, labeling them as good, bad, or neutral based on their historical behavior. By analyzing IP reputation, organizations and online platforms can enhance their security measures, preventing potential threats and safeguarding against malicious activities.
– Sponsored Links –
Threat Intelligence
The Speed Test app checks an IP against a global database of malicious IP addresses based on a comprehensive list of threat intelligence criteria including the following:
| Tor | If the IP address is associated with a node on the Tor network |
| VPN | If an IP addresses is VPN. There are approx. 2.6M IP addresses updated daily. This is available to Business and Enterprise users only. |
| iCloud Relay | If an IP address belongs to Apple’s iCloud relay service |
| Proxy | If the IP address is a known proxy, includes HTTP/HTTPS/SSL/SOCKS/CONNECT and transparent proxies |
| Datacenter | If any IP addresses that belong to a datacenter including all cloud providers. Can be useful for detecting automated/bot traffic. |
| Anonymous | If either one of Tor or Proxy is true |
| Known Attacker | If an IP address is a known source of malicious activity, i.e. attacks, malware, botnet activity etc. |
| Known Abuser | If the IP address is a known source of abuse i.e. spam, harvesters, registration bots and other nuisance bots etc. |
| Threat | If either one of known Abuser or Known Attacker is true |
| Bogon | If an IP address is a bogon. |
| Blocklists | If an IP address has been reported to one or more blocklists. |
Read our blog article “IP Threat Intelligence Explained” to understand the potential security risk of any specific threat intelligence
– Sponsored Links –
– Sponsored Links –
Table of Contents
– Sponsored Links –
– Sponsored Links –
– Sponsored Links –